Counter Terrorism Surveillance Techniques

Ripa is the law governing the use of covert techniques by public authorities.
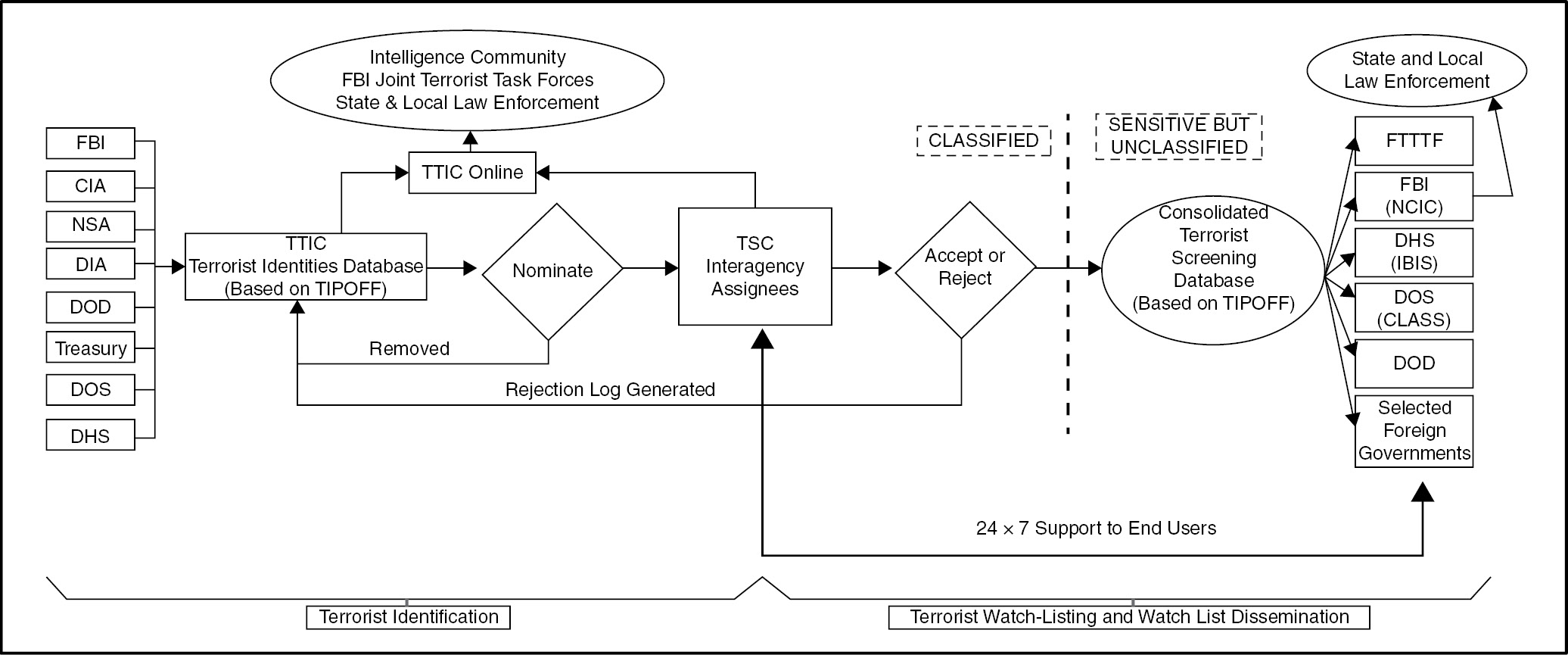
Counter terrorism surveillance techniques. Joint terrorism task forces jttfs serve as the coordinated action arms for federal state and local government response to terrorism threats in specific us geographic regions the fbi is the lead agency that oversees jttfs. But it was the sept. Public authorities involved in the prevention and investigation of acts of terrorism and potential terrorist conspiracies have shown great interest in ensuring that the records generated by communications service providers e g public and private companies providing telecommunications and. 11 2001 terrorist attacks that made counterterrorism a pillar of domestic and foreign policy in the u s.
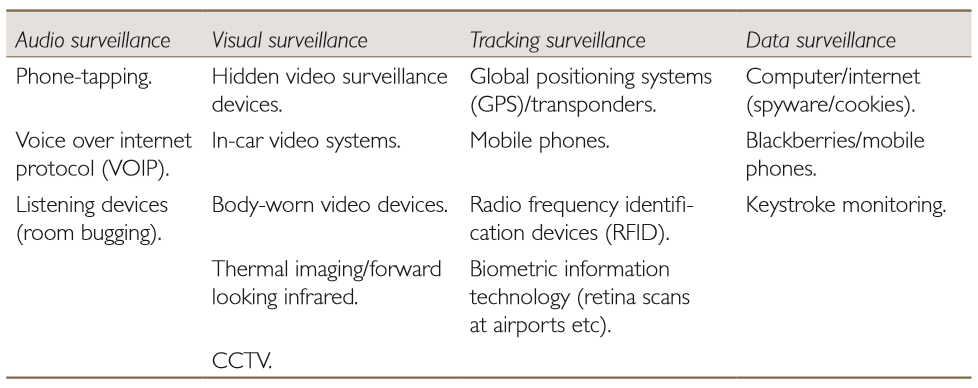
The benefits of a jttf include. Counter terrorism also spelled counterterrorism also known as anti terrorism incorporates the practice military tactics techniques and strategy that government military law enforcement business and intelligence agencies use to combat or prevent terrorism. Counter terrorism behavioural detection officer. To gather information about persons in such a way as not to alert the target means that the use of sits will normally involve an interference with the right to private life of the target and other persons.
A unique course in south east asia. Singapore kuala lumpur april may 2020. In fact one common denominator of all the different potential threats whether from lone wolves militant groups common criminals or the mentally disturbed is that those planning an operation all monitor their target in advance. Countersurveillance refers to measures undertaken to prevent surveillance including covert surveillance countersurveillance may include electronic methods such as technical surveillance counter measures the process of detecting surveillance devices including covert listening devices visual surveillance devices as well as countersurveillance software to thwart unwanted cybercrime including.
At the same time using the right counter surveillance tactics and techniques you can elude most forms of physical and electronic eavesdropping. Almost any criminal act from a purse snatching to a terrorist bombing involves some degree of pre operational surveillance. With the evolution of wireless and microchip technologies surveillance devices have become smaller cheaper and better than ever before. Surveillance and counter terrorism.
This module is a resource for lecturers surveillance and interception of communications metadata. Government has made fighting terrorism a priority since the early 1970s following the terrorist attacks on the 1972 summer olympics in munich germany and several airline hijackings. It will introduce you to behavioural detection through a major role playing exercise simulating counter terrorism scenario that comprises technical and human surveillance techniques. Counter terrorism strategy is a government s plan to use the instruments of national power to neutralize terrorists their.